gpg keys
Updated on 03 Oct 2020
Gnu Privacy Guard. GPG program can be used to create private / public keys for signing documents and git commits. They can not be used for ssh public / private keys. These are different and requires…
Encrypt File
To encrypt a file use -c flag.
gpg -c filename
You will be asked for a password! Once done, you will have a file called filename.gpg where
-c: means to use symmetric encryption with a password. Default is AES128.
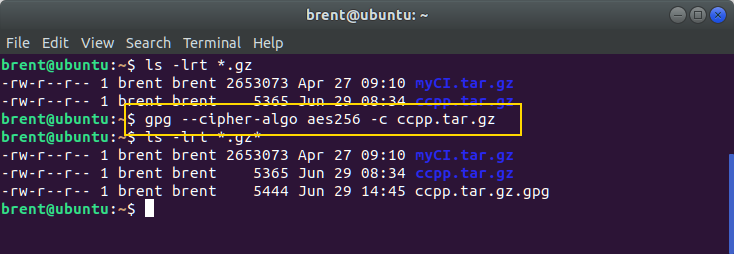
If you want to use AES256, then use the following command
gpg --cipher-algo aes256 -c filename
You can find other --cipher-algo options on the manpages.
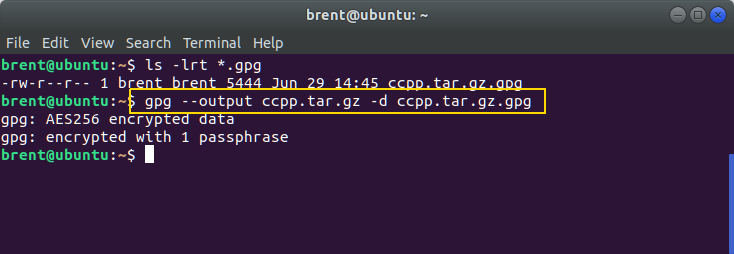
Decrypt File
To decrypt a file use -d and --output. Without the --output, gpg will simply display the file contents on the screen.
gpg --output ccpp.tar.gz -d ccpp.tar.gz.gpg
This will decrypt the file, and once again you’ll be prompted for a password. If you have only just encrypted the file then the system will remember the password and you wont be prompted for it.
--output: is the option for the output file-d: is for decrypt
Important
You must supply the options first before the command.
--outputis an option-dis a command-cis a command
Supplying passwords in bash
It could be that you wish to run gpg from a shell script, which will also require the use of a password. To do that, use --passphrase option.
gpg --passphrase test123 -c test1.tar.gz
Generating a public / private key pair
A PGP public / private key can be used to sign a document or a git commit (i.e. prove you’re the one who made it) or decrypt messages intended only for you, among other things.
gpg --gen-key
You will need to add in a few details such as name and email address. The email address will be used as an Id later on.
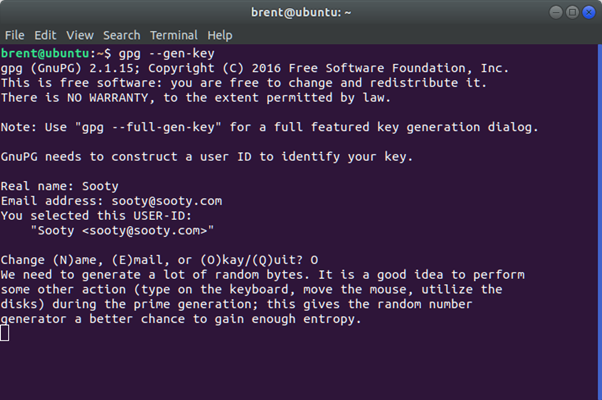
Next you will be presented with a screen to enter your password.
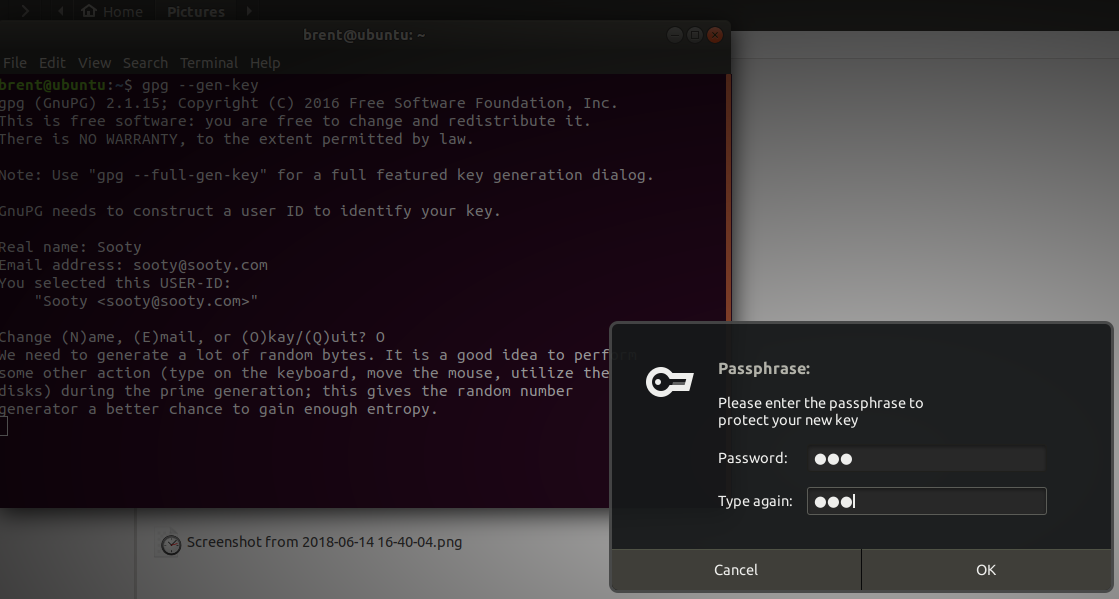
When all finished, you will have something that looks like this
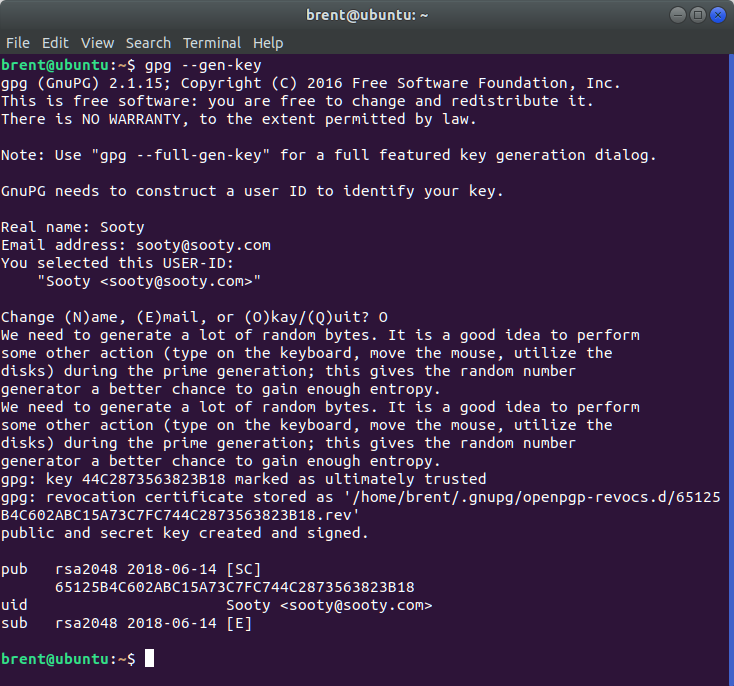
On a server there might be issues, so I recommend generating the keys on your local machine and importing them on a target machine. Also some servers won’t let you remove the pass phrase.
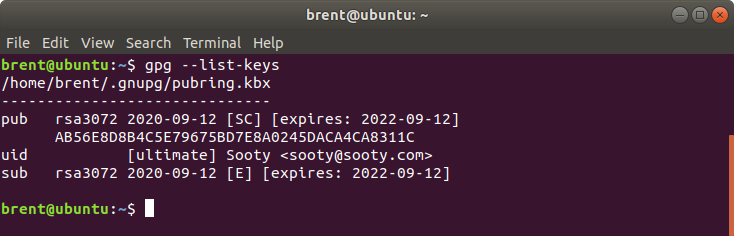
Listing Keys
You can list your keys with these commands
gpg --list-keysgpg --list-secret-keys
Exporting Keys
We can export keys as well. We might need to export the public key, and we do that like this: (First we might need to list the keys, then export the one we want).
gpg --list-keys
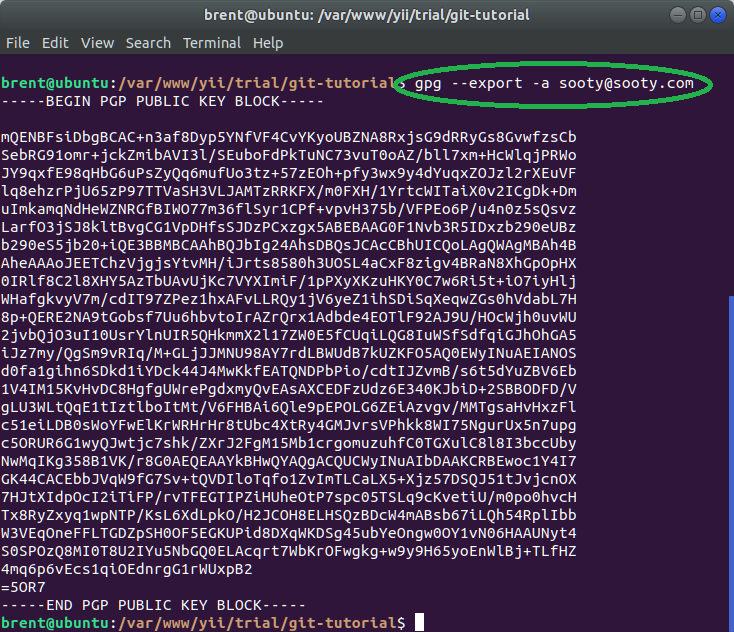
gpg --export -a sooty@sooty.com
The -a option means that we will export the key as 7bit ascii. Without it, we would get some crazy binary display like what we have displayed below…
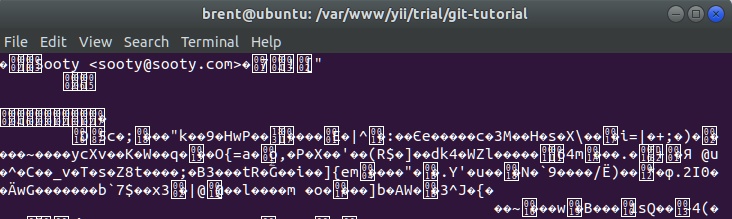
When you export with the the -a option, then we’ll get more of a plain text file.
You can also export your private keys for safe storing or back-up if necessary.
gpg --export-secret-keys -a sooty@sooty.com
You can leave the Key ID blank and you will get ALL the private keys. Exporting will typically be done to a file, so you’d probably be piping the out like this:
gpg --export-key -a sooty@sooty.com > sooty.pub
Importing a key
You can import a key into your keystore with the following command.
gpg --import sooty.pub
You can import private keys (especially if the server does not support the creation of keys without pass phrases)
gpg --import public.key
gpg --allow-secret-key-import --import private.key
Deleting a key
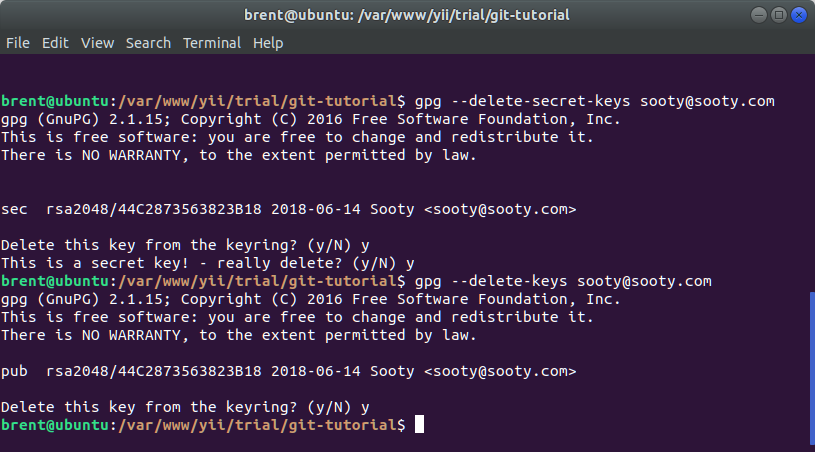
You can also delete keys, but make sure you delete the secret key first!
gpg --delete-secret-keys sooty@sooty.com
gpg --delete-keys sooty@sooty.com
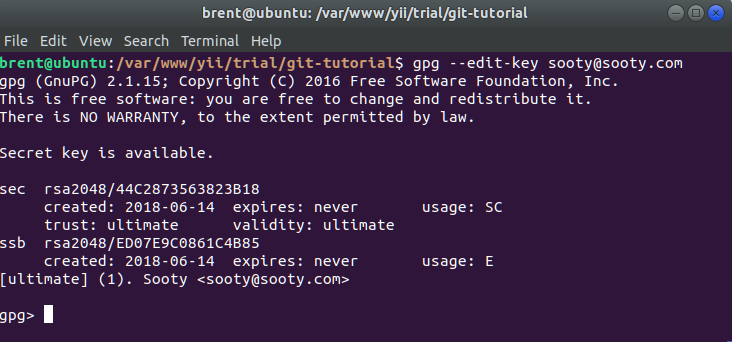
Editing a key (removing password)
We can also edit a key. The most likely reason for this is to remove the password. We can use the following command.
gpg --edit-key sooty@sooty.com
From here we can type help and see a list of commands available for us. The command to change the password is passwd, and you simply need to enter a blank password at the prompt. However, be warned that gpg may prompt you 2-3 times to make sure you want a blank password.